| Interfaces > Software > Manage Intune Endpoints |
From the Manage Intune Endpoints interface, you can see managed devices from Intune.
The Manage Intune Endpoints interface is located under the Software/Endpoints menu button.
You can manage devices, e.g. send client commands, see compliance status, manage assigned software and monitor install status and install / uninstall applications from multiple devices, users and or groups.
 |
Many Intune objects, including devices, are stored in the SoftwareCentral database. Because of this, you may experience a delay before new devices show up in SoftwareCentral. Use the "Can't find a device?" button to request devices directly from Intune. |
Use the search bar in the left menu to look up a user or device. You can search by:
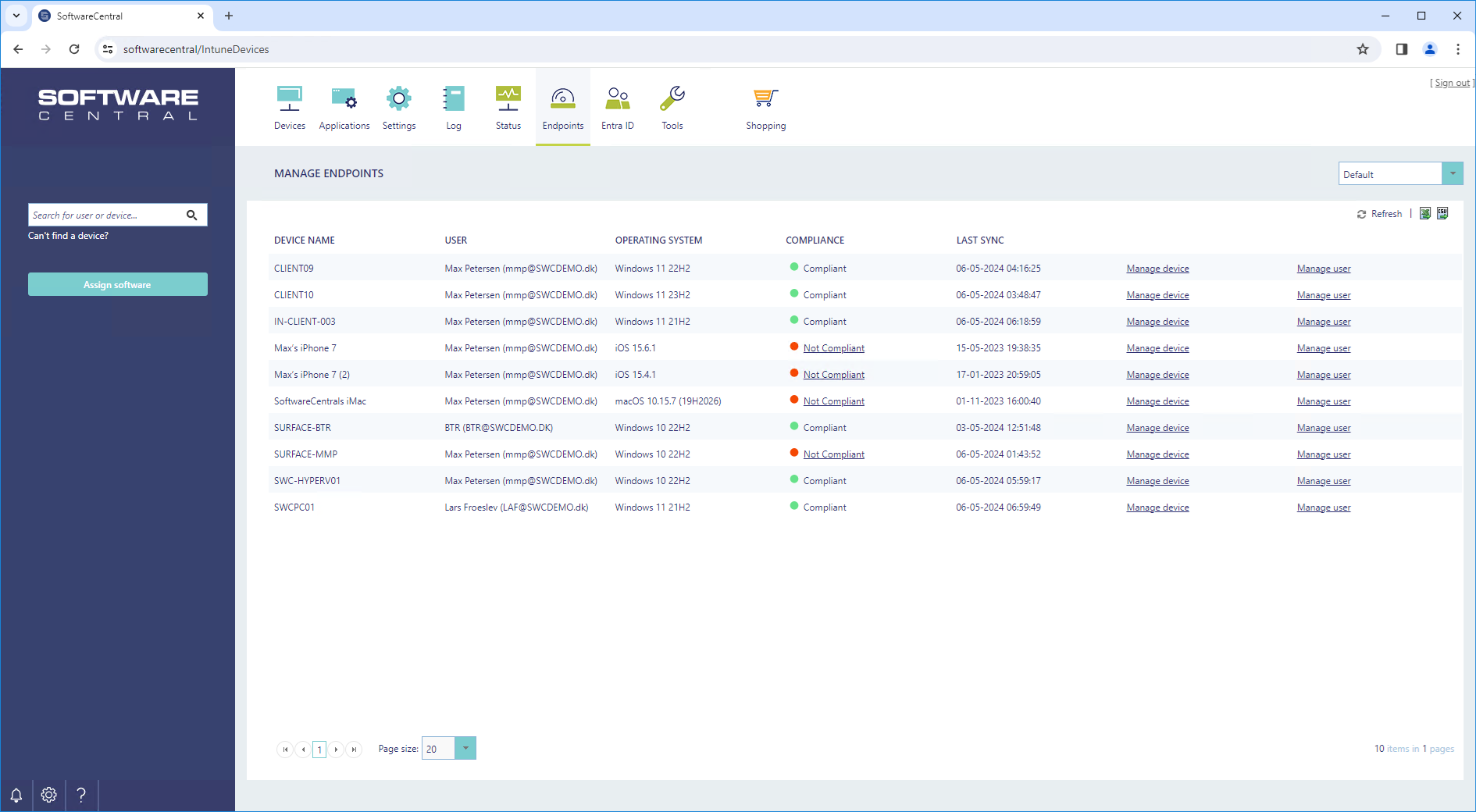
When you click on a device, a new window will open. From this window you have access to various tabs with tools to manage the device.
The device info tab gives an overview of common device information such as model, operating system version etc.
From the properties section, you can change the device ownership type. You can choose between Personal and Corporate.
The device ownership type determines which data Intune collects about the device and which Device Actions there will be available.
See and change the primary user of the device. If no user are selected, the device will be considered a shared device.
Click on the "Show recovery keys" button to open a window with the Bitlocker recovery key(s) for the device.

From the Device Actions tab there are multiple device actions that can be performed on the selected device. The available device actions will depend on your permissions, the device type and on the device ownership type. See a list of available actions below.
All action buttons will open a prompt, asking you to confirm the action. Some actions will also require additional inputs.
The Device Action Log displays the last device actions performed on this device. It may also contain important information such as new passcodes and recovery keys.

| Device Action | Available on | Description |
|---|---|---|
| Retire | Windows, Mac, iOS, Android | Removes company data managed by Intune. The user's personal data is not removed. |
| Wipe | Windows, iOS, Android | Factory reset returns the device to its default settings. This removes all personal and company data and settings from this device. You can choose whether to keep the device enrolled and the user account associated with this device. You cannot revert this action. |
| Delete | Windows, Mac, iOS, Android | Delete the device from Intune. You will no longer be able to view or manage the device from the Intune portal. The device will no longer be allowed to access your company's corporate resources. Company data may be wiped from the device if the device tries to check-in after it is deleted. |
| Sync | Windows, Mac, iOS, Android | SoftwareCentral will attempt to check in with the device. If successful, it will sync current actions or policies to the device. |
| Restart | Windows | Reboots the device. Users will not be automatically notified of the restart, and might lose unsaved work. |
| Fresh Start | Windows | This will remove all preloaded Win32 apps. You can choose whether to retain user data on the device. |
| Quick Scan | Windows | Windows Defender quick scan looks at all the locations on the device where there could be malware registered to start with the system, such as registry keys and known Windows startup folders. A quick scan helps provide strong coverage for both malware that starts with the system and kernel-level malware. |
| Full Scan | Windows | Windows Defender full scan checks all files and running programs on the device hard disk for malware. This scan could take longer than one hour. |
| Update Windows Defender security intelligence | Windows | Updates Windows Defender malware definitions for the device. |
| Rename Device | Corporate owned device, Windows, Mac | This is only available for corporate owned devices. Renames the device. |
| Remote Lock | Mac, iOS, Android | This action is intended to lock lost devices. While the device is locked, it will be unusable. For Mac's a six-digit recovery pin will be generated and displayed in the Device Action Log for 7 days. This PIN will be required to restore functionality to this device. Be sure to give the PIN to the device owner. For iOS and Android devices, users with the passcode will be able to unlock the device. |
| Remove Passcode | iOS | Removes the passcode. Users will be able to access the device without a passcode until a new one is set. |
| Send Custom Notification | iOS, Android | Sends a custom notification with your own title and message. Custom notifications might be visible on lock screen and to Android apps. Be careful when using them to share sensitive information. The title can be no longer than 50 characters. The Body can be no longer than 500 characters. |
| Reset Passcode | Android | Resets the passcode for the device. A new passcode will be generated and displayed in the Device Action Log for 7 days. |
The assigned software tab displays software assigned to this device.
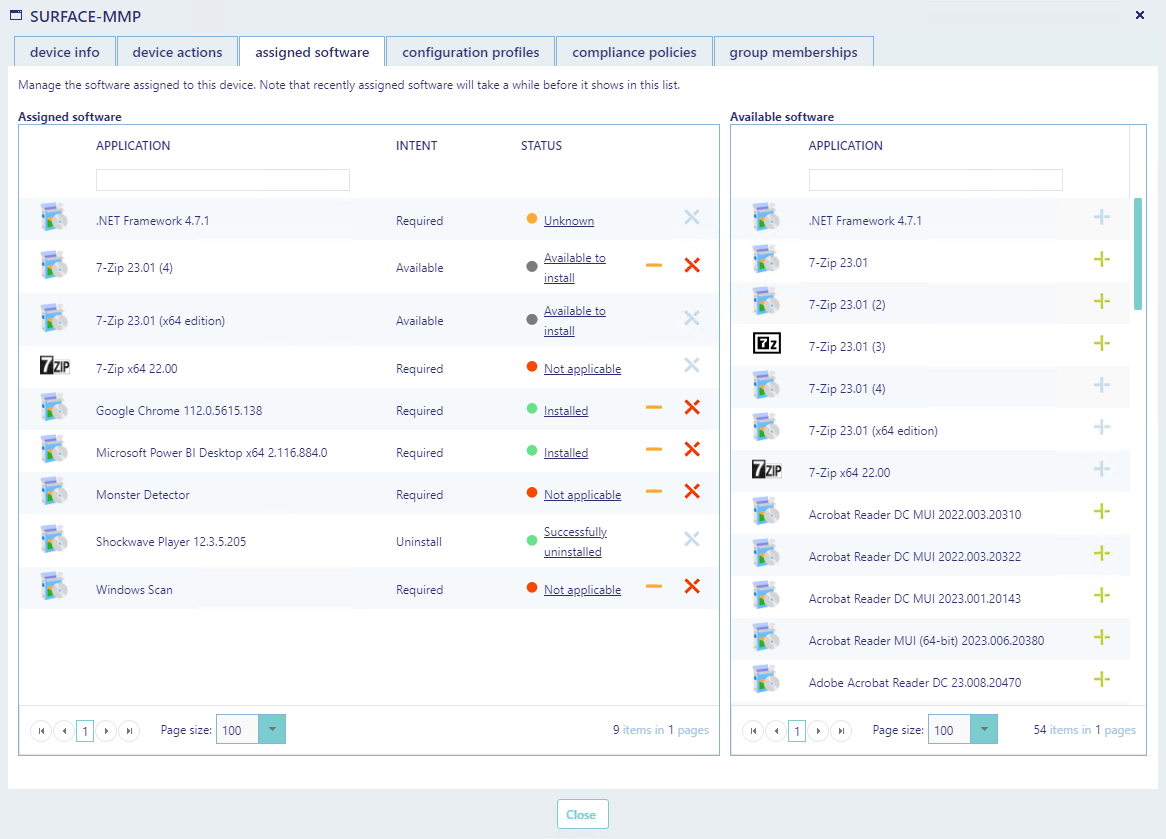
In the first grid (to the left) you can see software assigned to the device. You can see the intent (Required, available or uninstall) and the status.
If you click on the status, a window with detailed information will open. This can be helpful to troubleshoot why an installation has failed.
In the example below, we can for instance see that the installation of an app failed because the device did not meet the minimum operating system version requirement.

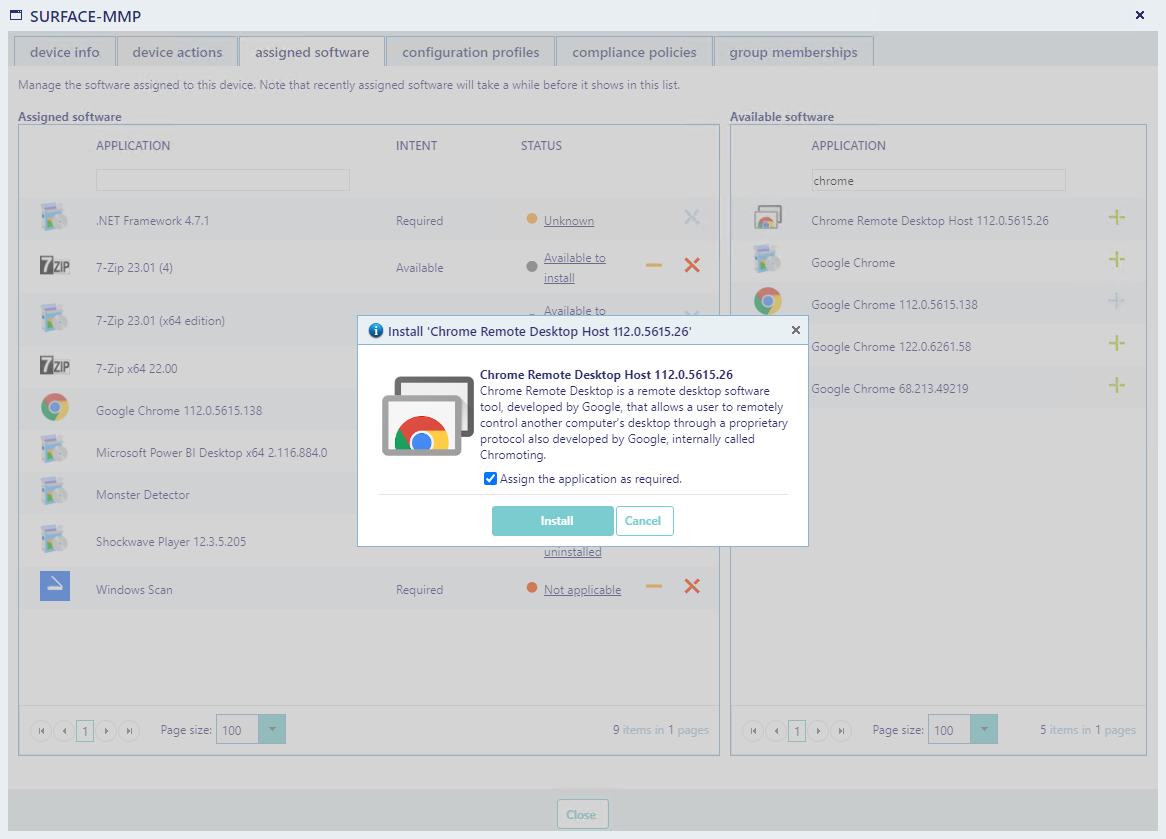
You can assign applications from the grid to the right by clicking on the green plus icon.
Before the app is assigned a window will open asking you to confirm the action.
You can choose to assign the app as required. If this is selected, the app will be installed on the users device, without user interaction. Meaning that the user will not have to go into the company portal to install the app. The user cannot choose to uninstall required apps.
If you do not assign the app as required, the app will be made available in the company portal, but will not be automatically installed.
The configuration profiles tab displays configuration profiles assigned to the device.
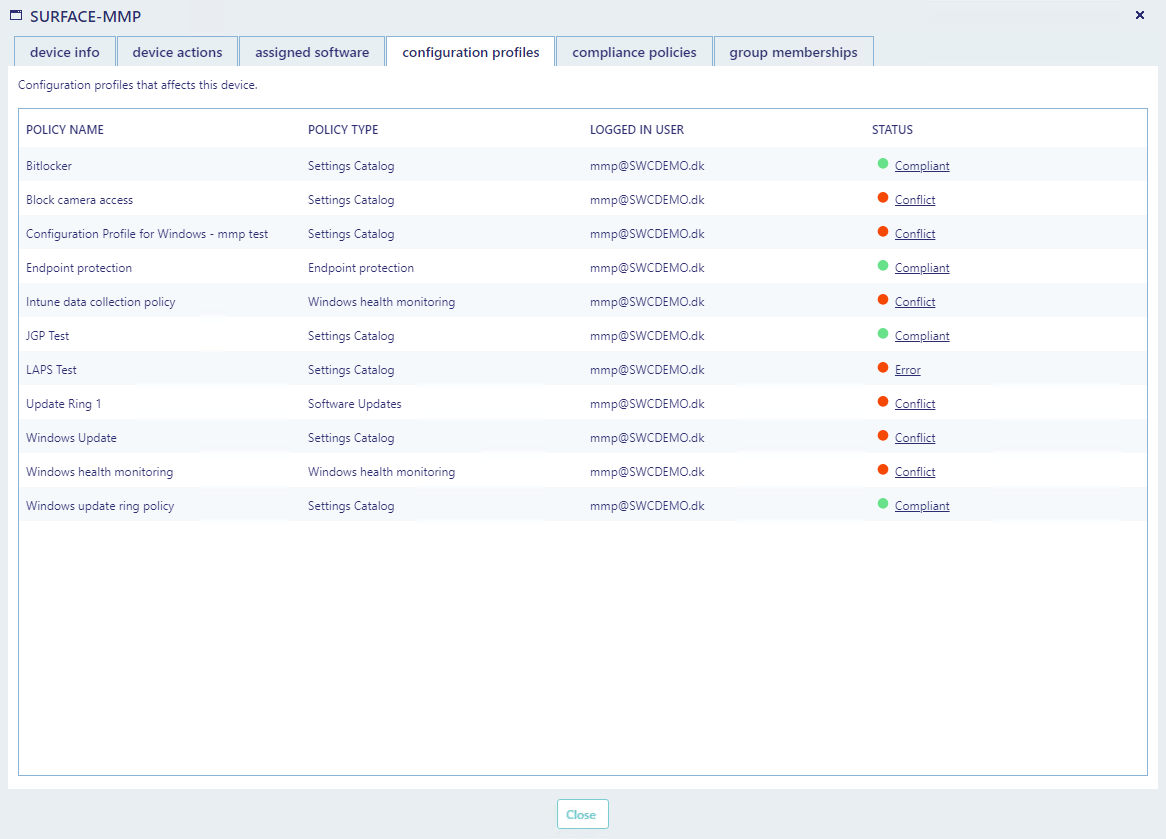
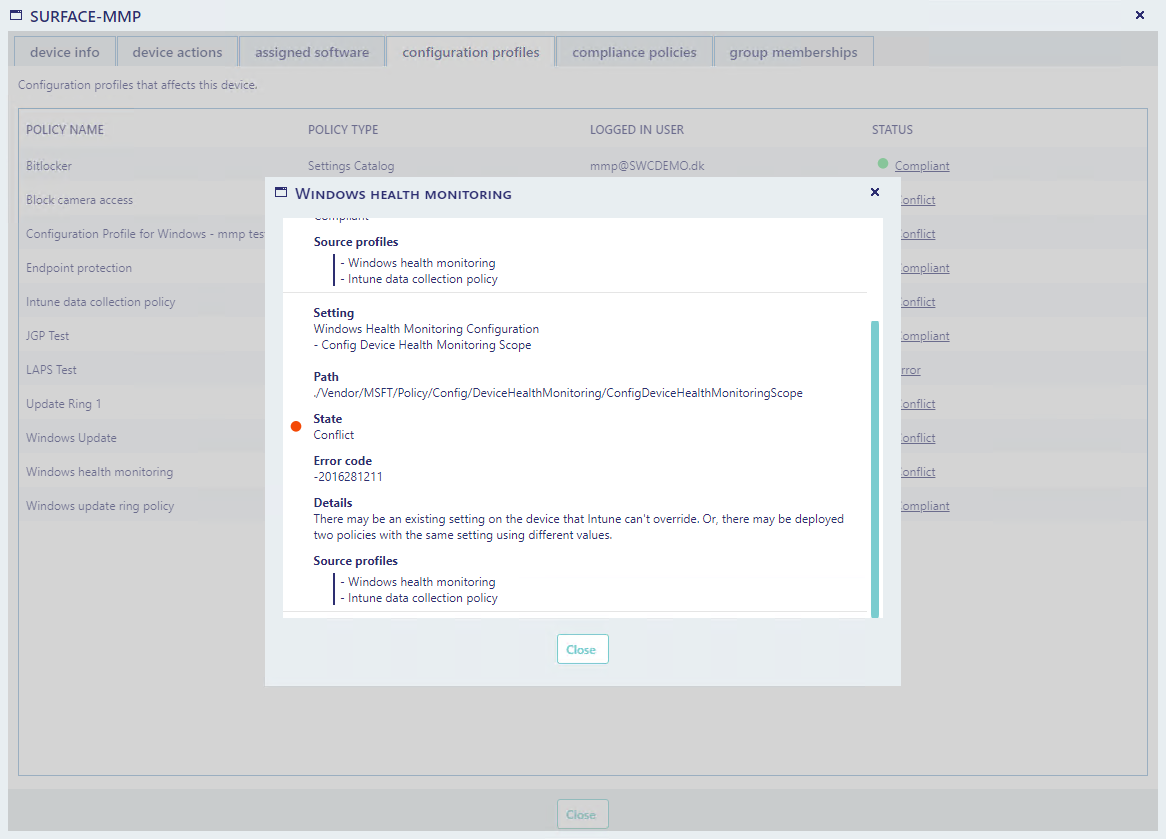
From the status column, you can click on a status to see detailed information on why the configuration profile has failed.
In the example below, you can see a configuration profile that has a setting that is in conflict with another configuration profile.
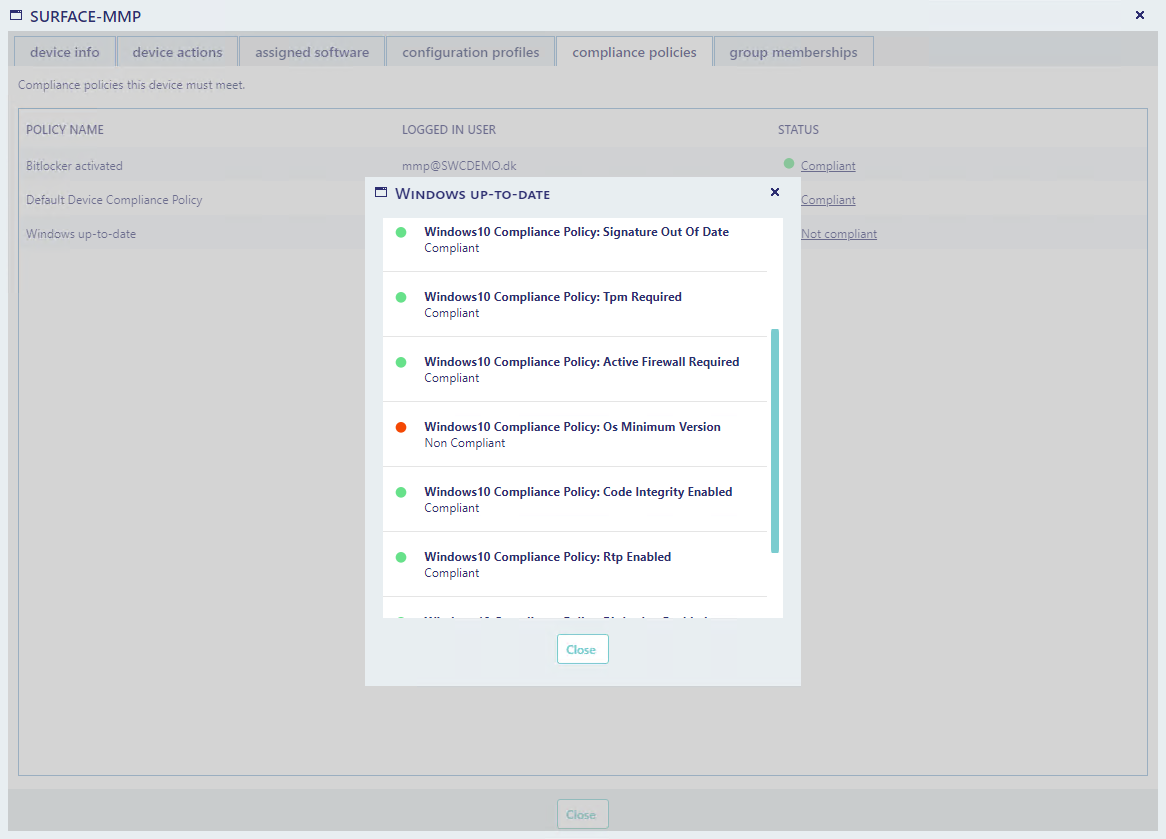
From the compliance policies tab you can see compliance polices assigned to the device.

From the status column, you can click on a status to see detailed information on why the compliance policy is not compliant.
In the example below, you can see that the current device dot meet the minimum operating system version to be comliant.
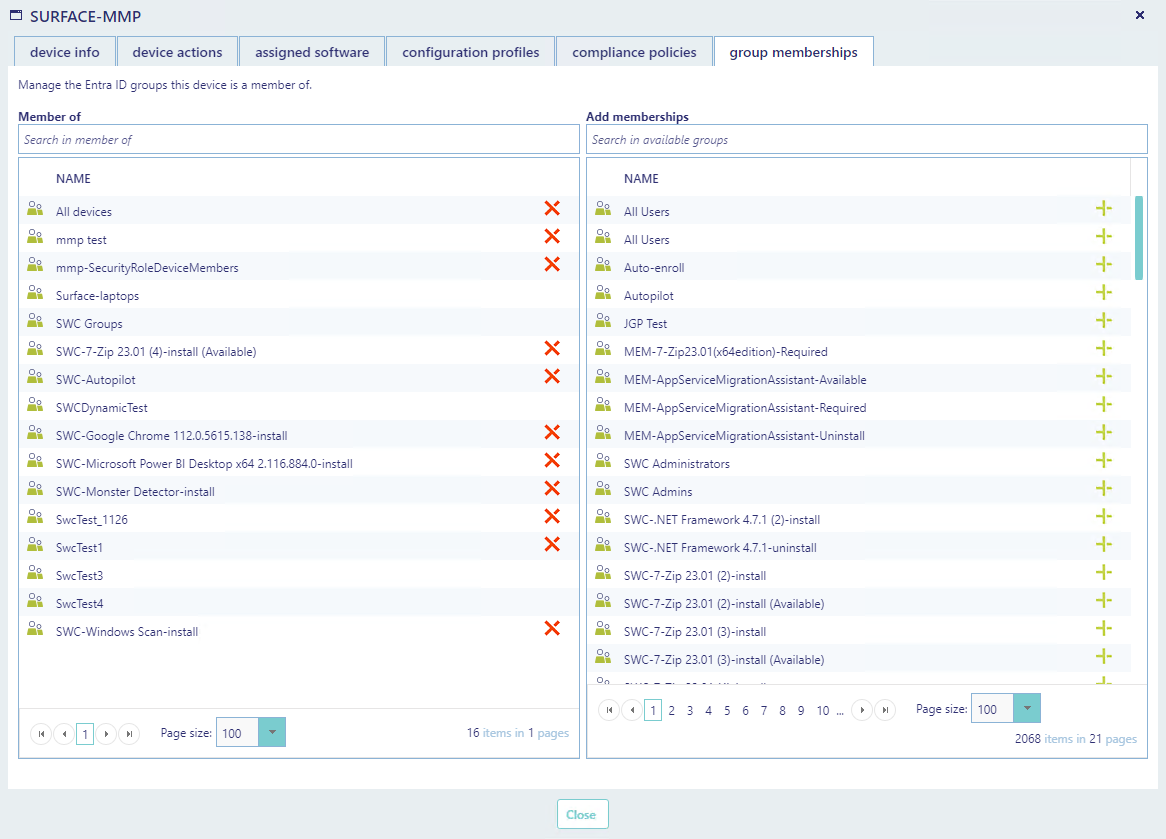
From the group memberships tab, you can see all Entra ID groups the device is a member of.
The device can not be removed from all groups. This depends on your permissions, the group type and the membership type.
You can also add the device to new groups from the grid to the right. Click on the green plus button to add the device to a group.
You will always be prompted before a device is added to or removed from a group.