

This is the list of required permissions for Microsoft Intune.
offline_access
openid
profile
Device.ReadWrite.All
DeviceManagementConfiguration.ReadWrite.All
DeviceManagementServiceConfig.ReadWrite.All
DeviceManagementManagedDevices.ReadWrite.All
DeviceManagementManagedDevices.PrivilegedOperations.All
WindowsUpdates.ReadWrite.All
BitlockerKey.Read.All
Application.ReadWrite.All
DeviceManagementApps.ReadWrite.All
Group.ReadWrite.All
Directory.Read.All
GroupMember.ReadWrite.All
RoleManagement.ReadWrite.Directory (only required to add members to role-assignable groups)
User.ReadWrite.All
Auditlog.Read.All
UserAuthenticationMethod.ReadWrite.All
UserAuthenticationMethod.ReadWrite.All
Mail.Send (Note that the service accounts for Intune tenants much have an active mailbox)
Mail.Send (This is only required, if you do not want to send mails on behalf of the service accounts)
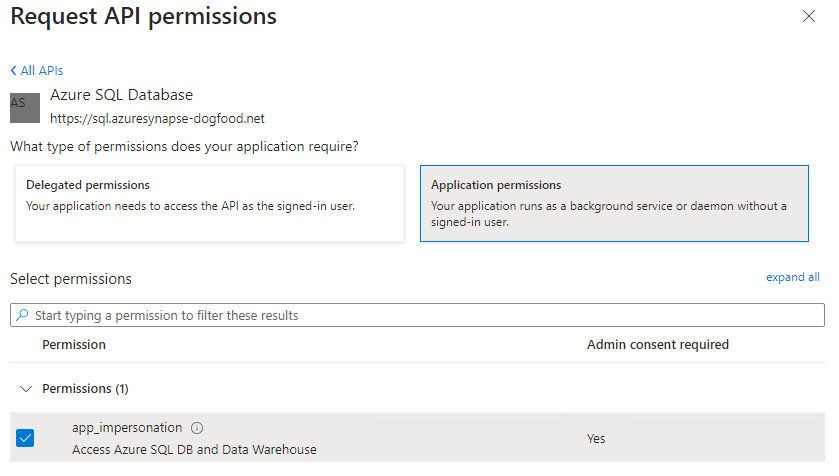
If your database is located in Azure, the following application permission is required:
Azure SQL Database - app_impersonation
If you cannot find this permission in the Azure portal, try the following fix:
1. Create an Azure SQL database and add yourself as either an admin or a user.
2. Login to that database with Microsoft SQL Management Studio using your Entra ID credentials.
3. You can now search for the permission "Azure SQL Database".
When you select "Azure SQL Database", choose "Application permissions" and "app_impersonation".
A service account is required to read bitlocker recovery keys, reset user passwords and in some scenarios to send mails. If you do not need these features, you do not have to add a service account.
 |
The service account must be created in Azure. It cannot be a synced on-prem account. The service account must have multi factor authentication disabled. |
The service account defined under settings must be a member of one of the following roles in order to read bitlocker recovery keys:
Use the below snippet to add the required permissions to your app registration manifest. Remember to grant admin consent after you have updated the manifest.
| Manifest |
Copy Code
|
|---|---|
"requiredResourceAccess": [
{
"resourceAppId": "022907d3-0f1b-48f7-badc-1ba6abab6d66",
"resourceAccess": [
{
"id": "c39ef2d1-04ce-46dc-8b5f-e9a5c60f0fc9",
"type": "Role"
}
]
},
{
"resourceAppId": "00000003-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "14dad69e-099b-42c9-810b-d002981feec1",
"type": "Scope"
},
{
"id": "7427e0e9-2fba-42fe-b0c0-848c9e6a8182",
"type": "Scope"
},
{
"id": "e1fe6dd8-ba31-4d61-89e7-88639da4683d",
"type": "Scope"
},
{
"id": "1bfefb4e-e0b5-418b-a88f-73c46d2cc8e9",
"type": "Role"
},
{
"id": "e383f46e-2787-4529-855e-0e479a3ffac0",
"type": "Scope"
},
{
"id": "37f7f235-527c-4136-accd-4a02d197296e",
"type": "Scope"
},
{
"id": "64a6cdd6-aab1-4aaf-94b8-3cc8405e90d0",
"type": "Scope"
},
{
"id": "b27a61ec-b99c-4d6a-b126-c4375d08ae30",
"type": "Scope"
},
{
"id": "62a82d76-70ea-41e2-9197-370581804d09",
"type": "Role"
},
{
"id": "9e3f62cf-ca93-4989-b6ce-bf83c28f9fe8",
"type": "Role"
},
{
"id": "2f51be20-0bb4-4fed-bf7b-db946066c75e",
"type": "Role"
},
{
"id": "741f803b-c850-494e-b5df-cde7c675a1ca",
"type": "Role"
},
{
"id": "b0afded3-3588-46d8-8b3d-9842eff778da",
"type": "Role"
},
{
"id": "7ab1d382-f21e-4acd-a863-ba3e13f7da61",
"type": "Role"
},
{
"id": "1138cb37-bd11-4084-a2b7-9f71582aeddb",
"type": "Role"
},
{
"id": "78145de6-330d-4800-a6ce-494ff2d33d07",
"type": "Role"
},
{
"id": "9241abd9-d0e6-425a-bd4f-47ba86e767a4",
"type": "Role"
},
{
"id": "5b07b0dd-2377-4e44-a38d-703f09a0dc3c",
"type": "Role"
},
{
"id": "243333ab-4d21-40cb-a475-36241daa0842",
"type": "Role"
},
{
"id": "5ac13192-7ace-4fcf-b828-1a26f28068ee",
"type": "Role"
},
{
"id": "dbaae8cf-10b5-4b86-a4a1-f871c94c6695",
"type": "Role"
},
{
"id": "b7887744-6746-4312-813d-72daeaee7e2d",
"type": "Scope"
},
{
"id": "7dd1be58-6e76-4401-bf8d-31d1e8180d5b",
"type": "Role"
},
{
"id": "50483e42-d915-4231-9639-7fdb7fd190e5",
"type": "Role"
}
]
}
],
|
|