

 |
The steps in this guide can all be performed automatically when installing / updating SoftwareCentral. |
This guide describes how to configure SoftwareCentral to connect to Microsoft Intune.
SoftwareCentral connects to Microsoft Intune via the Microsoft Graph API. This is done by creating an App Registration in the Azure Portal and linking this App Registration to your SoftwareCentral installation.
SoftwareCentral can connect to multiple Intune tenants.
 |
If you have not configured SoftwareCentral to run with https, you must do this before you proceed. |
SoftwareCentral accesses Intune as an application. Users of SoftwareCentral gets direct access to Intune and their accounts do not need access to Intune. Note that you are responsible for having Intune licenses for your users.
You can grant users access to Intune interfaces in SoftwareCentral and delegate resources with the SoftwareCentral Security Roles and Package Security Groups.
Your SoftwareCentral installation needs to authenticate against Intune. To do this a SSL certificate is required.
 |
If you already have created a certificate for another tenant, you must use the existing certificate. It can be found at "[InstallDir]\Uploads\Certifcates\UploadToIntune_SoftwareCentral.cer". |
You can create a self-signed certificate directly from SoftwareCentral or acquire your own certificate from your preferred certificate authority.
You will need a .pfx file with the certificate and the private key.
You will also need a .cer file with the certificate and only the public key, not the private key.
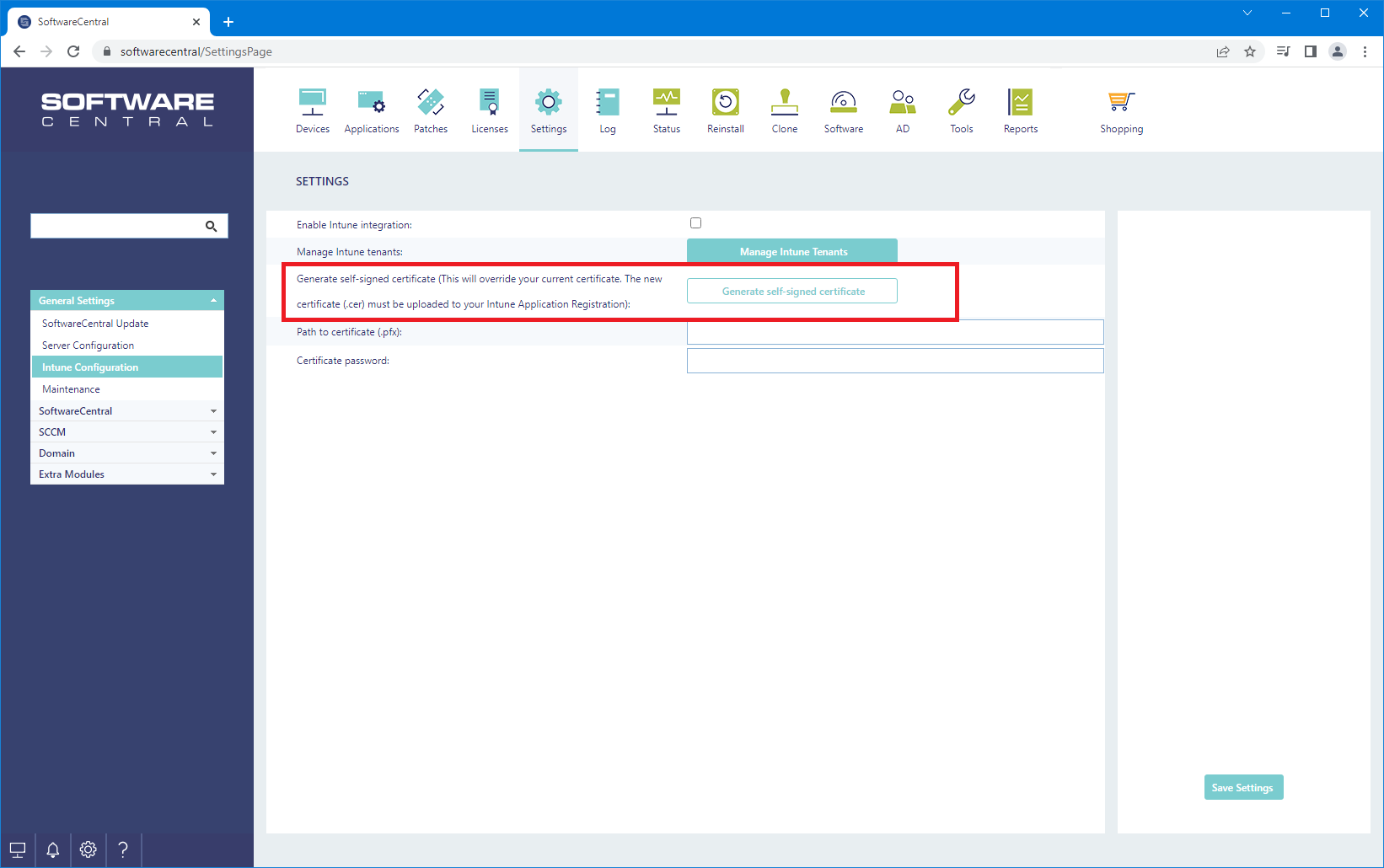
SoftwareCentral can create a self-signed certificate from Settings -> Settings -> General Settings -> Intune Configuration -> Generate self-signed certificate.
Or the certificate can be created via the Intune configurator, that will launch the first time you start SoftwareCentral after the installation.
When you click on the "Generate self-signed certificate", you will be prompted for a password. Enter a strong password for the certificate and save this password.
A certificate file named "UploadToIntune_SoftwareCentral.cer" will be downloaded. This is the certificate you upload to Intune later in this guide. The certificate itself with the private key is stored in the SoftwareCentral installation folder under "Uploads\Certifcates\StoreLocally_SoftwareCentral.pfx".
Once you have downloaded the certificate file, click on the "Save Settings" button, to save the certificate path and password.
The same certificate is used for all your Intune tenants. If you need the existing certificate's .cer file, you can find it in the SoftwareCentral installation folder under "Uploads\Certifcates\UploadToIntune_SoftwareCentral.cer".
If you use your own certificate, you must enter the location and password to the .pfx file.
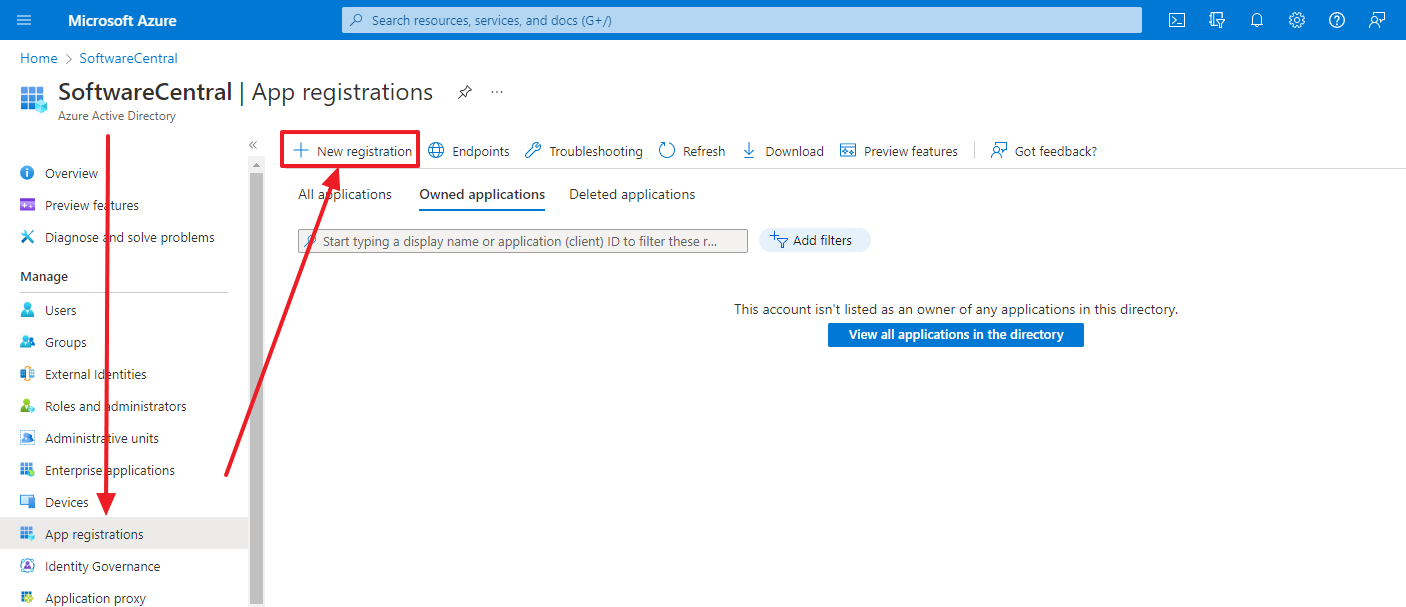
You need to setup an App Registration in your Azure Portal to allow SoftwareCentral to connect to your Intune.
Go to the Azure Portal -> Entra ID-> App registrations -> New registration:
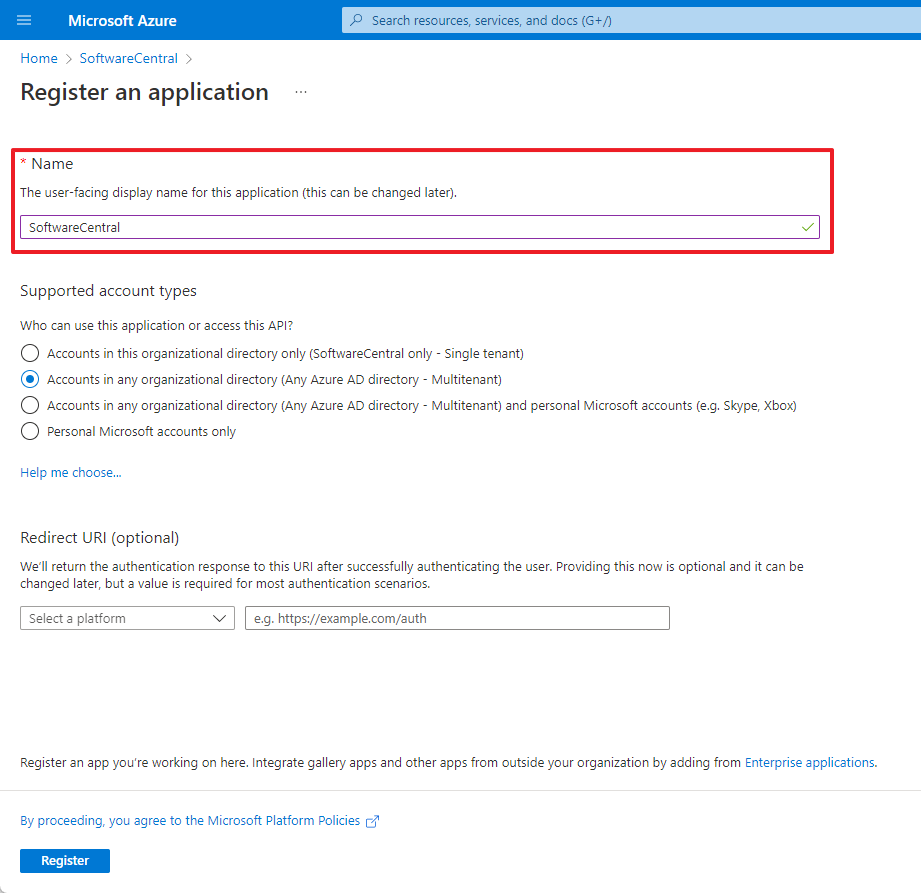
Give your App Registration a name.
If you require multi-tenant support, select that.
Click "Register" to save:
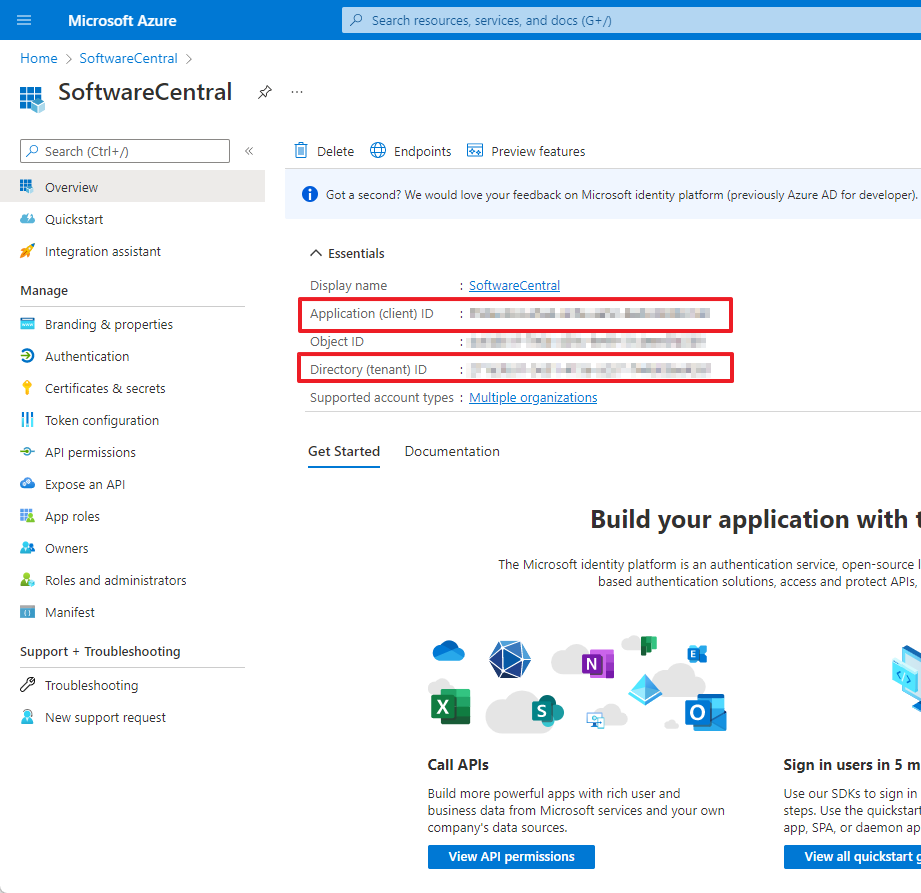
The Application Registration will now be created and opened. On the overview page, note the Application and Directory ID. They will be needed later during the setup.
Next you must go to "Certificates and secrets" and upload the .cer file:
If you have generated the certificate through SoftwareCentral, then this is the certificate file named "UploadToIntune_SoftwareCentral.cer" that you downloaded earlier from SoftwareCentral.
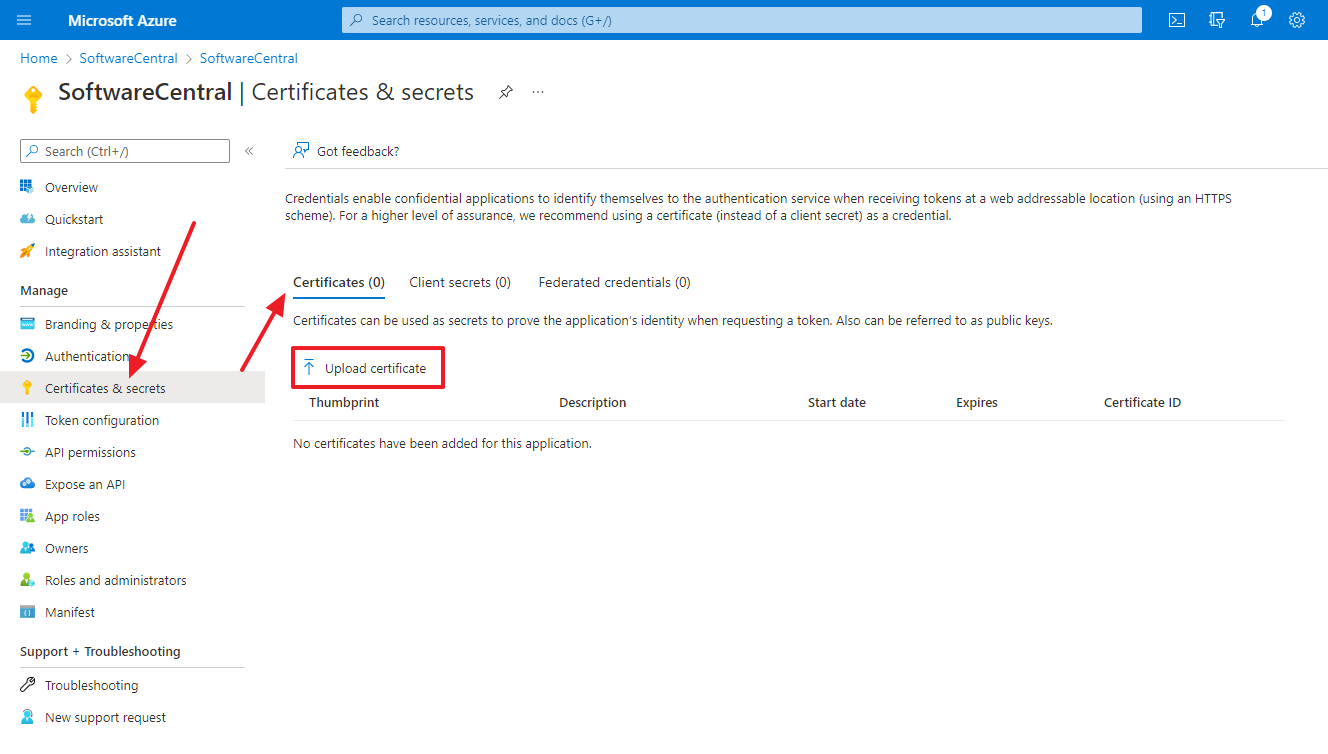
You must now grant permissions for the application. Go to "API permissions" and click on "Add a permission":
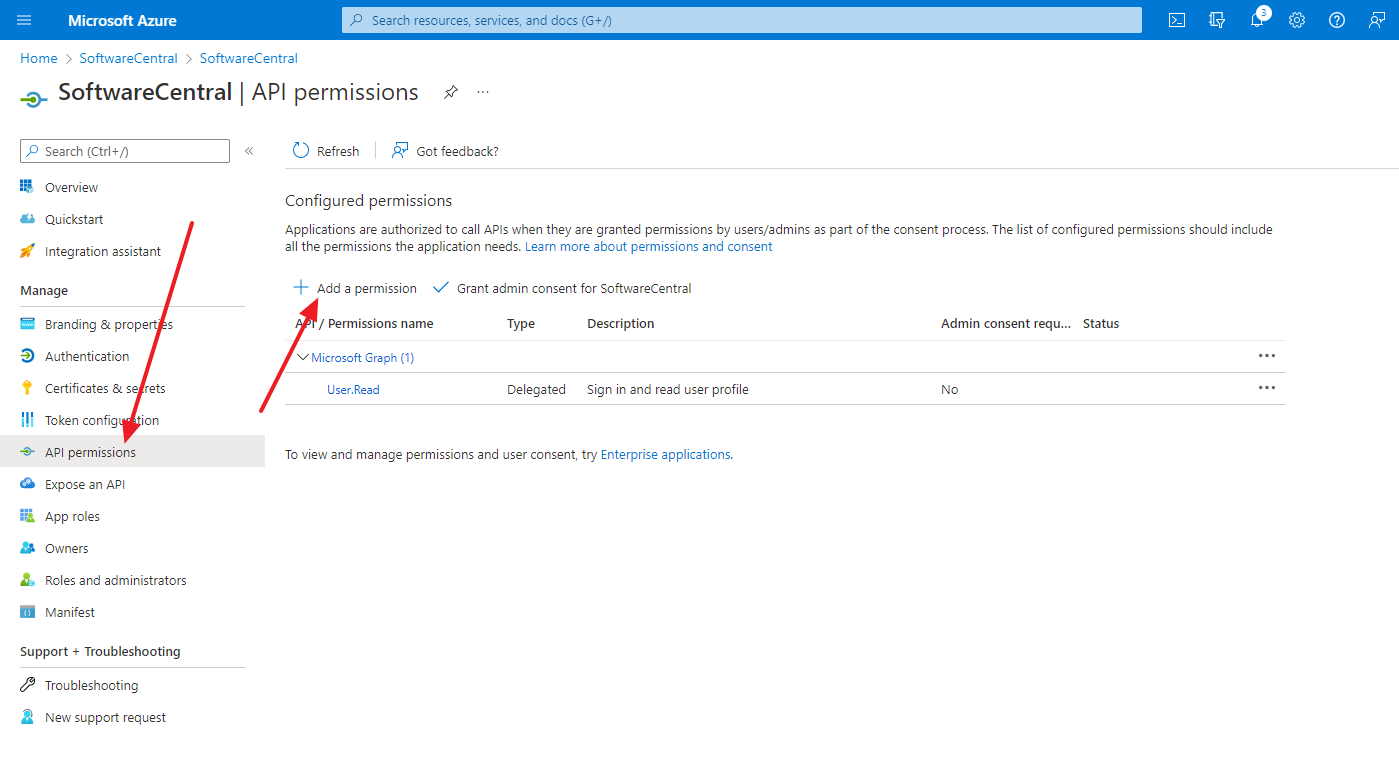
Select "Microsoft Graph":
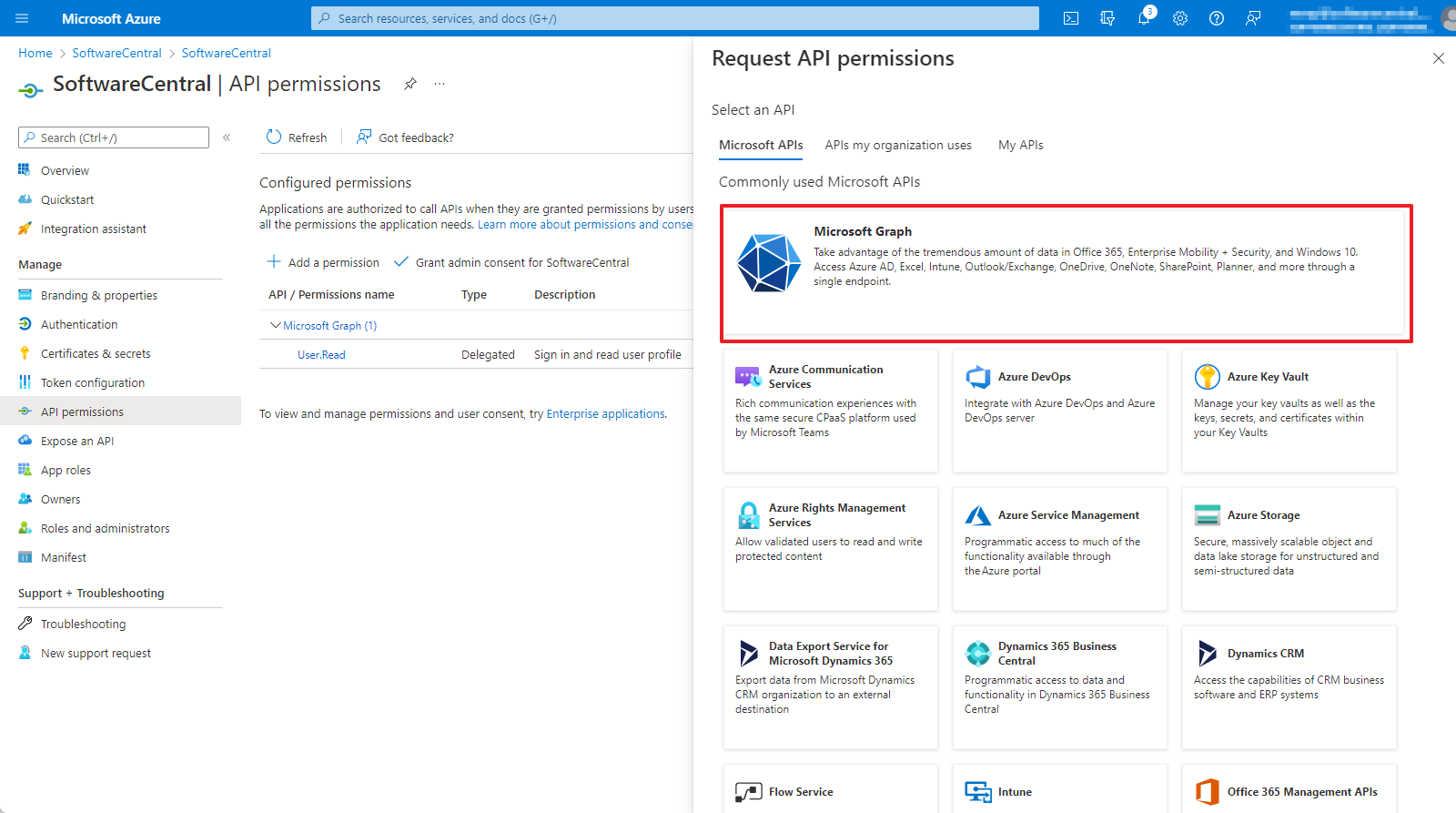
SoftwareCentral requires both delegated and application permissions.
For a complete list of permissions, refer to the chapter Intune Permissions.
Once all permissions has been selected, you must grant admin consent:
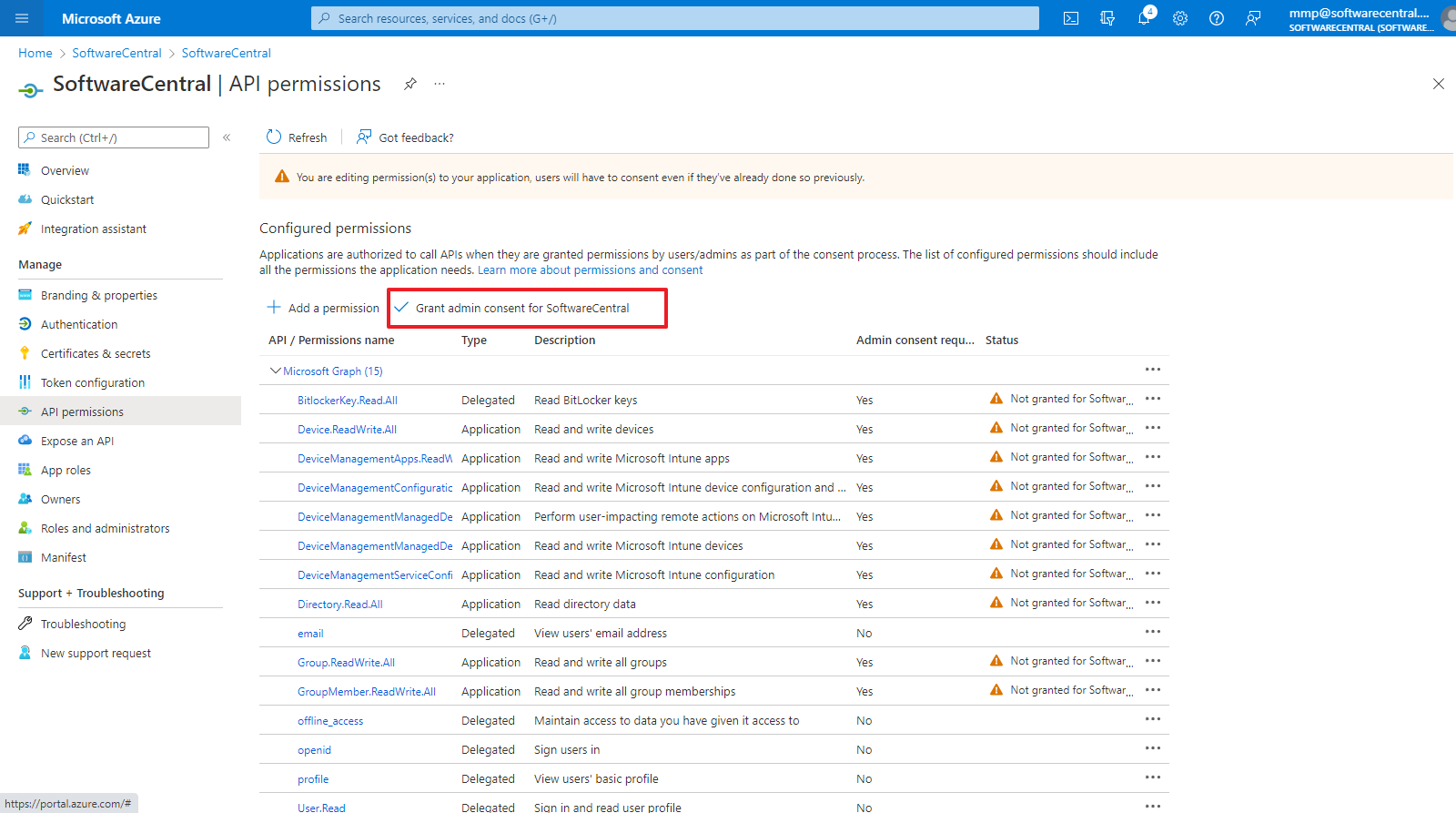
 |
After a permission has been added, it may take Azure several minutes before the application gets the new rights. |
Some data in Intune is not available to applications, but only to users. This include BitLocker keys and resetting user passwords. If you do not want to use these features, you can omit the service account.
Therefore a service account is needed. The service account must be a member of one of the following roles:
 |
The service account can not use multi factor authentication. |
 |
The service account must be created in Azure. It cannot be an account synchronized from a local Active Directory. |
You are now ready to add the tenant to SoftwareCentral.
Go to the SoftwareCentral console. Open Settings -> Settings -> Intune Configuration and click on "Manage Intune Tenants":
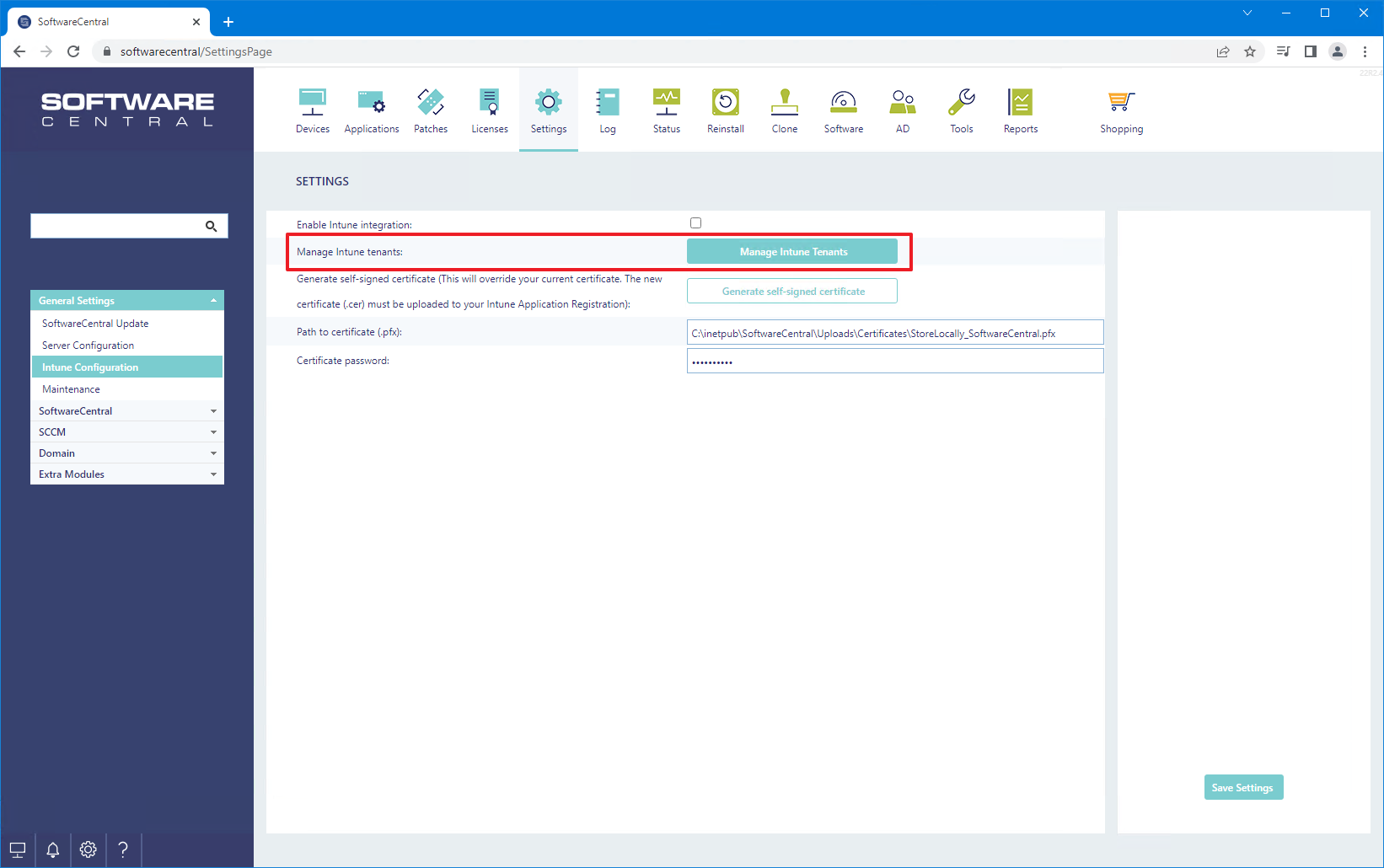
A new window will open. Here you must enter all the fields.
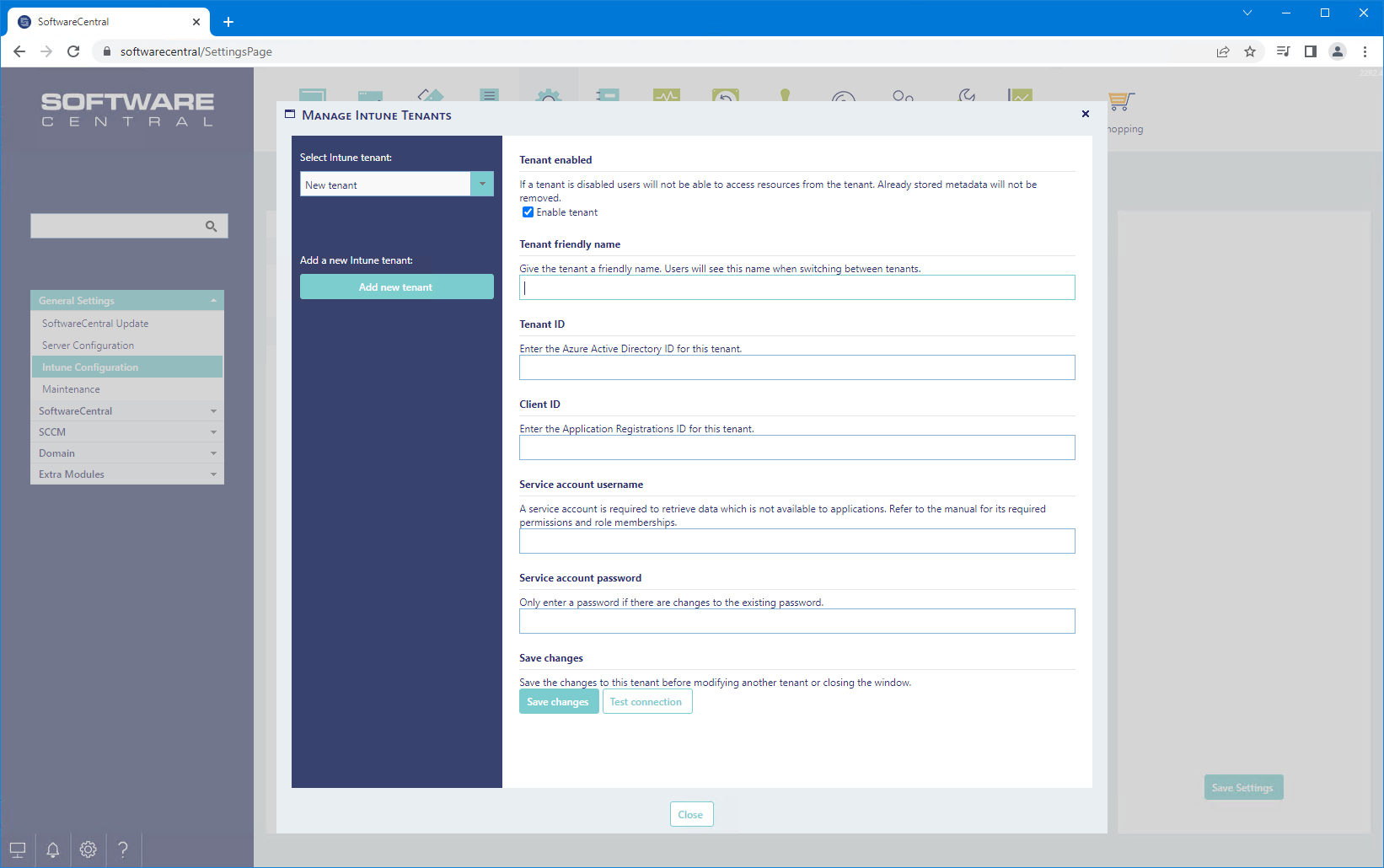
Once you have filled in everything you can click on "Test connection" to verify that everything is okay or not.
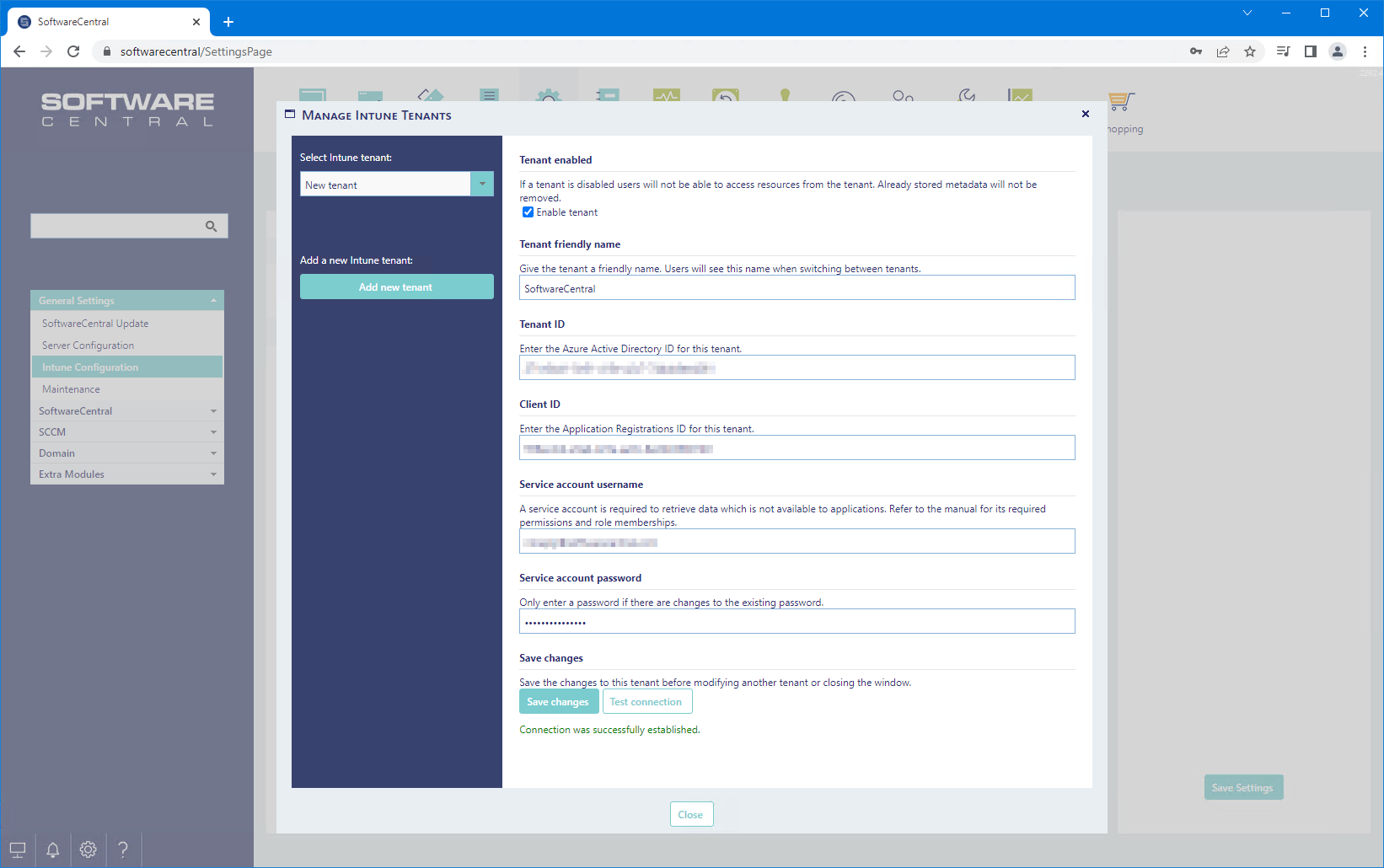
Any issues will be reported in the interface after you have tested the connection:
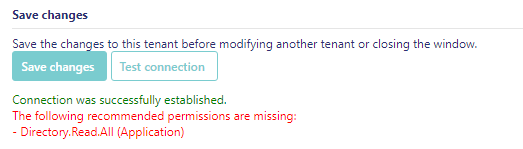
Here is an example where a permission is missing:
Click on the "Save changes" button to save the Intune tenant.
Finally, go to "Maintenance" and first click on "Clear Cache" and then "Restart SoftwareCentral".
SoftwareCentral caches data from Intune. The cache is updated every hour. If you are missing a resource, it will show up after an hour.
If you are performing tests, you can go to Settings -> Service Manager and restart the service. This till trigger the caching to refresh.
You can now assign the new Intune tenant to your Security Roles.
You can also assign Intune applications to Package Security Groups.